In this article I am going to tell you everything about SSL that what it is why we need it, technical and non technical aspects of SSL etc.. This article covers the introduction, SSL certificate, Encryption, process of encryption and how your browser interact and trust that certificate provided by the website you are visiting.
Existence of SSL
There are basically 2 aspects of SSl. One is Encryption and second is Identification. Now encryption is what you hide the content of the data sent from one machine to another machine. It is done by changing the content of the data in identical to garbage form which is human readable but not human understandable. It is exactly like speaking in different languages with what one person is not familiar. I am Indian if someone speaks in Russian language, it is not understandable by me. So here Russian language is like encrypted language for me. However if I get a translator and he/she translates that Russian language into Hindi then I can say that now that is understandable by me. So it is said that message has been decrypted. Identification is related to trust. In the previous scenario, how can I trust the translator who is converting Russian language to Hindi? Is she/he legitimate ? Can I trust him/her? In the digital world, it is something like this. Your machine has to trust the SSL certificate (security mechanism), provided by the website via an SSL certificate issuing vendor.
Encryption Explained
To understand scenario lets take an example directly. Let’s suppose you are sending a credit card details to the company(any company/ online purchasing website etc..).
So here is the scenario, you are on the left and you will be sent your card details to the other machine. Now there can be 2 scenarios.
1. Without SSL
2. With SSL
1. Without SSL
2. With SSL
Without SSL : In this scenario there can be another machine in your network which can grab the details sent by another machine shown in below figure.

As you know that this scenario is without SSL. So in this case any malicious user lying in the same network can perform a MITM attack or any other attack which contains a simple network traffic monitoring, can able to grab your credit card number or any personal detail. So it is always necessary to use SSL, otherwise any other machine between you and any other network may have an ability to capture your private data. So SSL works as a barrier in that. It creates a tunneling technique. Here is the other scenario.
With SSL : SSL puts the security mechanism on the network layer before you transfer the data. As below picture shows, It creates a barrier or tunnel by which user can transfer his any data to the other network. Now this time malicious user(lying on the same network) will see the tunnel. So he won’t be able to grab your private data passing through the tunnel.
As you saw in the picture, a malicious user is going to grab the data passing through the tunnel, but here she/he will get encrypted data not the real plain text data. So data can be grabbed but now it’s only a garbage value for the cracker/hacker as she/he will never come to know that what exactly the real data was. In order to decrypt the data she/he will need an encryption key which they will never get.
Lets see how HTTPS look like in the coding. Here I am giving you the twitter ‘s signing page source code. As you all know that every sign in page contains POST method to pass our data to the server. Every POST method is defined under the form. Here is a form action method listed below in the picture.

As you can see here that action in the html code is embedded with HTTPS which is known as a secure HTTP method. So it confirms that your login credentials are secure once you click on the submit button in order to log in. The actual process of Encryption is enclosed below.
The ‘Actual’ Process of Encryption
Everything we are doing is a digital process which is happening in no matter of time but in reality its really a long process which has many steps. At each step there are integrity, authenticity and process of mechanism are involved.
The ‘Actual’ Process of Encryption
Everything we are doing is a digital process which is happening in no matter of time but in reality its really a long process which has many steps. At each step there are integrity, authenticity and process of mechanism are involved.
As soon as you hit on the button to log in, First, it says that now your machine(computer) is ready for the encryption process. Secondly, the server will send one certificate to your machine which has to be digitally signed by you. If you don’t call the process of login, the server will not send your certificate as its not actually needed, because you are not going to give any credentials to the server. Thirdly, your machine digitally signs the certificate in backend and it sends to the server. Indirectly it tells the server that, “I am ready now, kindly start the encryption process please.“. Fourthly, the server receives the certificate signed by your machine and then it starts the encryption process at client’s end. Lastly, the server actually encrypts all the messages passed by the client and after successful encryption all the data is passed through the secure tunnel at the server end.
This whole process is called Handshake.
The ‘Actual’ Process of Encryption Unleashed In Detail
1. How Your machine chooses an encryption process? Which are the different possibilities/methods involved in this process?
Encryption process includes basically 3 parts.
1. Encrypting Message : There are many algorithms in world for encrypting the message. Most famous algorithms are AES, 3-DES and RC4. People generally use any one of these methods to encrypt the message. Each algorithm contains many operations such as shiftrows, subbytes, mixcoloumns, addroundkey etc.. That is the only strength of these algorithms. If the algorithm has more operations, it provides better encryption. It is the way of encrypting data between client & the server.
2. Hashing : It is known as a message authentication code. This term is used in cryptography. It includes a hash function combined with a secret key. That is used for authentication as well as data integrity too. The strength of the hashing depends on the cryptographic function used in that along with the key. Generally HMAC-MD5 and HMAC-SHA1 are used for the hashing.
3. Choosing Key for encryption: It contains a key exchange mechanism such as RSA, DSA & Diffie-Hellman algorithm. One can get more information on this part by searching TLS and Public Key Cryptography on Wikipedia.
Scenario : Lets suppose computer on the left side is about to send the “Hellow World” message to the server and it chooses AEC cipher method, HMAC-MD5 hashing technique along with RSA key. Along with all these 3 data it also sends the version number of SSL used by your machine for TLS(Transport Layer Security) and random number. A random number is nothing but the master calculation which is used to do all other calculation for the encryption process. And All this information is passed to the server.

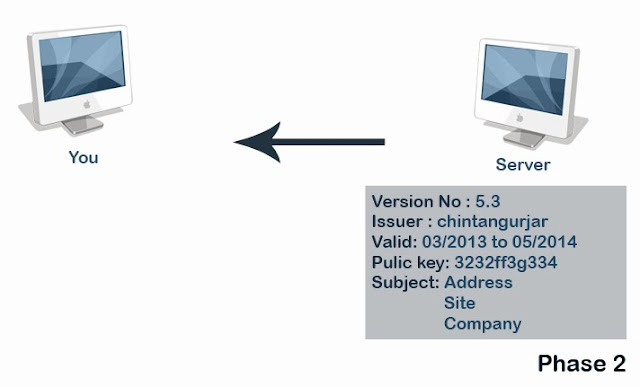
In the next stage, the server sends a certificate to the client. This certificate has the information such as version number, serial number, signature, issuer, validity, subject, IssuerUniqueIdentifier, SubjectUniqueIdentifier, Signature algorithm, signature value, public key etc..
1. Encrypting Message : There are many algorithms in world for encrypting the message. Most famous algorithms are AES, 3-DES and RC4. People generally use any one of these methods to encrypt the message. Each algorithm contains many operations such as shiftrows, subbytes, mixcoloumns, addroundkey etc.. That is the only strength of these algorithms. If the algorithm has more operations, it provides better encryption. It is the way of encrypting data between client & the server.
2. Hashing : It is known as a message authentication code. This term is used in cryptography. It includes a hash function combined with a secret key. That is used for authentication as well as data integrity too. The strength of the hashing depends on the cryptographic function used in that along with the key. Generally HMAC-MD5 and HMAC-SHA1 are used for the hashing.
3. Choosing Key for encryption: It contains a key exchange mechanism such as RSA, DSA & Diffie-Hellman algorithm. One can get more information on this part by searching TLS and Public Key Cryptography on Wikipedia.
Scenario : Lets suppose computer on the left side is about to send the “Hellow World” message to the server and it chooses AEC cipher method, HMAC-MD5 hashing technique along with RSA key. Along with all these 3 data it also sends the version number of SSL used by your machine for TLS(Transport Layer Security) and random number. A random number is nothing but the master calculation which is used to do all other calculation for the encryption process. And All this information is passed to the server.

In the next stage, the server sends a certificate to the client. This certificate has the information such as version number, serial number, signature, issuer, validity, subject, IssuerUniqueIdentifier, SubjectUniqueIdentifier, Signature algorithm, signature value, public key etc..
In phase 3, your computer tells the server to start encryption. Here both machine have to take part in the conversation. There are 3 steps to accomplish this process.
1. Key Exchange – Here both the machines calculates the master secret code. And then on that master secret code will be used for the encryption process.
2. Change Original Text – Here your computer tells the server to change the original text written in order to send the server. In our case, it’s “hello world”. So the server actually receives confirmation of starting an encryption process and it starts the encryption process in order to generate cipher text of our given text.
3. Finish State – In the last stage of the process, your computer actually tells the server that all the messages have been encrypted now and ready to go.
After all these 3 stats happen, It sends the message to the data.
In phase 4 the server receives the messages came from the client side. And then it encrypts those messages and make it cipher text. Then the server tells client that I have finished encrypting your message. Then a message is sent back to the client is in encrypted form. So these both scenarios are mentioned in below pic together.

So this is the scenario of SSL if we take the real life scenario then SSl works somehow like below pic.
SSL Identification
Its another important thing which has to be considered while playing with SSL. It is all about the trust. It has to be make sure that the website with which you are corresponding is the real website which you are assuming and you trust. It doesn’t mean that you are having SSL certificate, then you are secure. Having an SSL certificate only is not enough thing. So that is why identification comes into play. It’s all about who you actually trust.
You might have seen below pic when you are trying to access any website on the internet. It represents SSL. There is a whole big process involved behind this dialogue box. Process behind this is somewhat like this.
1. First the website you are going to access over SSL has to go to the other organization which provides certificate authority. Then it will look into the details of the company/website and it will verify that the information is true about that company.
Its another important thing which has to be considered while playing with SSL. It is all about the trust. It has to be make sure that the website with which you are corresponding is the real website which you are assuming and you trust. It doesn’t mean that you are having SSL certificate, then you are secure. Having an SSL certificate only is not enough thing. So that is why identification comes into play. It’s all about who you actually trust.
You might have seen below pic when you are trying to access any website on the internet. It represents SSL. There is a whole big process involved behind this dialogue box. Process behind this is somewhat like this.
1. First the website you are going to access over SSL has to go to the other organization which provides certificate authority. Then it will look into the details of the company/website and it will verify that the information is true about that company.
To get the certificate from the certificate company has to give certain information about itself to that company. That information may include these:
1. Web the server name
2. Company name
3. Location of company
Then CA authority company checks whether this information is correct or incorrect. If it is correct then it goes to step 2.
2. Then that another company creates one certificate and digitally signs it with cryptographic methods explain in this article previously.
Certificate looks like this. Here is are different certificates.
The Certificate contains this information :
* Signature
* Signature Algorithm
* Version
* Serial Number
* Algorithm ID
* Issuer
* Identifier for issuer
* Identifier for company
* Public Key Information
* Signature
* Signature Algorithm
* Version
* Serial Number
* Algorithm ID
* Issuer
* Identifier for issuer
* Identifier for company
* Public Key Information
Key
Algorithm
* Validity
* Company Details
Now here signature is generated. Well certificate contains all this information. But the numbers used in all this information are taken by the HASHING algorithm and it does the calculations and it generates signature. So only number field contains from all this information, is taken by hashing algorithm in order to generate the signature. Then that number gets encrypted with the private key. So anyone who is holding a public key can verifies that number.
Algorithm
* Validity
* Company Details
Now here signature is generated. Well certificate contains all this information. But the numbers used in all this information are taken by the HASHING algorithm and it does the calculations and it generates signature. So only number field contains from all this information, is taken by hashing algorithm in order to generate the signature. Then that number gets encrypted with the private key. So anyone who is holding a public key can verifies that number.
3. Then they send the certificate to a company which you are going to access. Now certificate is installed on the server of the website which you are trying to access. Certificate generated in step 2 is given back to the company asked for that certificate. Let’s suppose it runs IIS/APACHE/TOMCAT web the server. So it installs that certificate on the web server. One can configure any of these web the server and use that certificate.
4. On the other hand when you are trying to access website, certificate comes from the website at your end. Your browser will verify the details of the certificate and if the information is true then your browser will also sign that certificate. Make sure your browser won’t sign the incorrect certificate. At the client side certificate looks like below: This will be used in the handshake.
5. When your browser gets certificate it verifies it with the world via signature and then it encrypts the data.
So thus how I simplified and unleashed SSL in front of the view. Now I will lead you to the practical demonstration that how you can generate your own SSL certificate and how to see that.
How To Generate SSL Certificate
We will download and install the required package to install SSL certificate. Then we will sign the certificate manually by giving a personal information to the certificate. After this has been completed, we will restart httpd service in order to run our SSL certificate successfully.
Step 1 : Downloading and installing required software
To generate an SSL certificate, OpenSSL and mod_ssl must be installed on the system. This tool may have already been installed in the apache however this varies from system to system. So we will install these tools by using the following command:
# yum install mod_ssl openssl
 |
| mod_ssl Installation process |
Step 2 : Sign Our SSL Certificate Manually
We will now use OpenSSL to sign our certificate. It is important to have this SSL certificate from a valid and trusted certificate providing authority if the use is for any company or organization. However, if it's for personal use then one can do it at home and there will be no need for a trusted company who provides a signed certificate to sign it.
We will have to follow the steps below to create a self signed certificate:
We will now use OpenSSL to sign our certificate. It is important to have this SSL certificate from a valid and trusted certificate providing authority if the use is for any company or organization. However, if it's for personal use then one can do it at home and there will be no need for a trusted company who provides a signed certificate to sign it.
We will have to follow the steps below to create a self signed certificate:
Create A Private Key
 |
| Generate Private Key |
CSR Generation
 |
| Certificate Generation |
Key Generation (Self Signed)
 |
| Figure 4 : Key Generation |
Put Files In Proper Location
Now that we have configured our task and put files into the right folder, we will now update the apache the server by updating the apache SSL configuration file which is the ssl.conf file. We will use the nano editor to update our ssl.conf file and change the path of key file where we have stored our files like certificate and key.
 |
| Changing key path in ssl.conf file |
The next step is to save and exit this file. After which we will start httpd service by typing the following command in the terminal.
 |
| Showing our self generated certificate digitally signed by us |
# /etc/init.d/httpd restart
Now that we have set up our secure socket layer, if we attempt to login to our the server machine through the client machine or attacking machine via the https protocol; it will ask for the authentication. Before the authentication. A dialogue box is shown which warns that "connection is not trusted and asks if they want to see the certificate which is going to be downloaded in the machine or if they want to stay in offline mode". Once the user clicks on the view certificate, it will display the certificate which was created earlier. This screenshot below illustrates this step:
It shows the issuer’s name, organization name and validity of the certificate. With this secure connection, if one logs in into the website or network, it will encrypt the plain text data and an attacker won't be able to capture straight away in the wireshark option.
Now that we have set up our secure socket layer, if we attempt to login to our the server machine through the client machine or attacking machine via the https protocol; it will ask for the authentication. Before the authentication. A dialogue box is shown which warns that "connection is not trusted and asks if they want to see the certificate which is going to be downloaded in the machine or if they want to stay in offline mode". Once the user clicks on the view certificate, it will display the certificate which was created earlier. This screenshot below illustrates this step:
It shows the issuer’s name, organization name and validity of the certificate. With this secure connection, if one logs in into the website or network, it will encrypt the plain text data and an attacker won't be able to capture straight away in the wireshark option.
Experiment : I have set up apache the server and I have performed MITM attack in which I am passing login credentials without SSL and with SSL. In both ways I captured Wireshark screenshots. Those screenshots are as bellows:
 |
| Authentication Credentialshave been captured in plaintext - WITHOUT SSL |
As you can see here one can capture your login credentials if you are not using SSL and not encrypting your data.
 |
| SSL Handshake is Being Done |
SSL handshake is being done now in the next picture you will see cipher text generated and passing through the network.
As you can see here credentials are encrypted now. No one can see the real credentials of the client passing through the network. Thus how SSL is useful to to encrypt the data.
Conclusion
SSL can give protection against man-in-the-middle attack. It can protect sensitive data such as login credentials, credit card details, home address other phone number etc.
References
1. http://pubs.vmware.com/view-51/index.jsp?topic=%2Fcom.vmware.view.installation.doc%2FGUID-B238BB47-D710-4DAB-945F-B54D46164FE0.html
2. http://validationcertificateinfo.blogspot.co.uk/2012/12/the-advantages-and-disadvantages-of.html
3. http://uk.godaddy.com/ssl/ssl-certificates.aspx
4. http://en.wikipedia.org/wiki/Transport_Layer_Security
5. https://developer.mozilla.org/en-US/docs/NSS
6. http://tools.ietf.org/html/rfc6101
7. http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_1-1/ssl.html