Portspoof is meant to be a lightweight, fast, portable and
secure addition to the any firewall system or security system. The general goal
of the program is to make the information gathering phase slow and bothersome
for your attackers as much it is only possible. This is quite a change to the
standard 5s Nmap scan, that will give a full view of your systems running
services.
So let’s
start directly. So this is how the common structure of portspoof. First I will
mention normal network structure without using portspoof and then with using
portspoof. Below figure shows the normal structure of my network.
Here when attacker scans the CentOS server’s
network then first request will be sent to Iptables and according to iptables
rule it will send the respond to the server. So currently in my iptables
standard rules have been set.
As you can see port 22 is open and any
connection thorough client machine to server’s ssh service is allowed. So if I
scan this network through NMAP from my KALI linux which I am considering as an
attacker’s machine then it will show me below result.
Now let’s check the network configuration with
portspoof. Make sure portspoof’s default port is 4444. You can change it
according to your need.
As we can see in the above picture
when an attacker sends an nmap scan request to the centos server, then first it
gets received to the iptables. Then rather than responding to the attacker
machine, iptables forward that request to the portspoof on 4444 port and it
enables portspoof to respond to the attacker’s machine in order to show all
65535 ports open.
Let’s Start
Demonstration …
Firstly I am flushing all the rules
of iptables and I am letting all packets allow into my network. To do so there
is a following command shown below:
Iptables –f
After giving this command if you
want to see the current policy then you can check it with below command.
iptables –l
Now it’s time to configure our
iptables with the portspoof. For that lets download and install portspoof. I
have downloaded rpm package of portspoof. Below command installs that package.
rpm –ivh portspoof-1.0-5.1.i686.rpm
|
Command/Command
Option
|
Description
|
|
rpm
|
rpm package
manager
|
|
-i
|
Install package
|
|
-v
|
Prints routine
process verbose information
|
|
-h
|
Print 50 hash
marks as the package archive is unpacked.
|
Next thing to do is to flush all the
current firewall rules. As we already checked previously we do not have any
rules set in our current firewall. So apply those iptables –f and –l command in
your server to cross verify our process.
Then as we can see from above pic
that our firewall is up and running and it is allowing all packets from any
network. Not it is time to forward those packets to portspoof in order to reply
the client machine. To do so command is as follow.
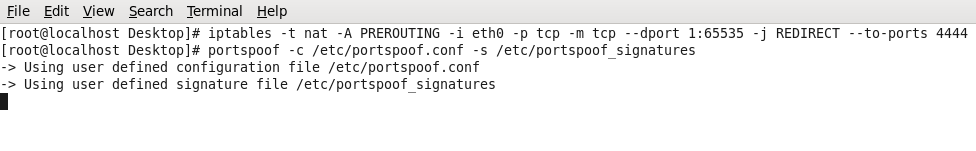
iptables –t nat –A
PREROUTING –i eth0 –p tcp –m tcp --dport 1:65535 –j REDIRECT --to-ports 4444
|
Command/Command
Option
|
Description
|
|
Iptables
|
Linux default
firewall.
|
|
-A
|
Appends the iptables
rule to the end of the specified chain. This is the command used to add a
rule when rule order in the chain does not matter.
|
|
-t
|
It specifies
the table name which we are going to use.
|
|
-i
|
Selecting the
interface.
|
|
-m
|
Additional
match options are also available through modules loaded by the iptables command. To use a match option module,
load the module by name using the -m
option, such as -m
|
|
-p
|
Sets the
default policy for the specified chain, so that when packets traverse an
entire chain without matching a rule, they are sent on to the specified
target, such as ACCEPT or DROP.
|
|
--dport
|
Destination
port
|
|
-j
|
Jump
|
|
--to-ports
|
Destination
port to forward.
|
Last few words in this command is
very important that first it will collect all the packets accepted by an
iptables and then it will forward it to the 4444 port which is a by default
port of our portspoof tool.
Now let’s scan the target.(Keep in
mind that we have not configured our portspoof.)
Now it shows that our host(CentOS)
is live and running but it is not showing any list of open port. It suggests
that we have successfully configured our iptables with the portspoof. So our
iptables is successfully sending all incoming packets to the portspoof. Now it
is time to configure portspoof.
Portspoof runs with its two main
files which is lying in /etc/
folder shown as below.
In config file, all the rules have
been written that how and what should portspoof reply to the client machine and
in signatures there are lots of signature of various scanning tools.
For example if I do normal nmap of 1
host, it will only show me port xyz is open and it will also show me port
number. But, if I use nmap with –sV command then it will also try to fetch the
service name which is used by the server and it will show me at the client
side. So these –sV and like these other signatures are detected by the
portspoof and it gives false results according to the request.
To start portspoof lets check the
help to determine which options are provided to us.
Two mandatory options are needed to
run the portspoof. Command to run portspoof is as follow.
portspoof –c /etc/portspoof.conf –s
/etc/portspoof_signatures
One you give this command it will
look like as follow.
Now it is time to scan from our
attacker machine(Kali Linux).
As you can see starting from 1st,
it will show all 65535 ports open. Actually these ports are not actually open
or even exists but thus how we are fooling attacker to make him see all 65535
ports are opened.
If you want to scan that host with
any signature within nmap then it will show as below. I am using nmap with –v
and –A option. Then result will be as follows.
If you can remember when we started
portspoof it was on verbose mode. So if we check that host machine now it will
show some information related to log that which kinds of threads have been
coming and which kind of signature reply that portspoof tool has given in
respond to that request. This information will show as follow.
Conclusion
Thus how you can fool the attacker
or a noob. If you configure this he will be confused and out of his mind that
which port is actually and legitimately open. If he is a pro noob then he will
start hunting from port 1st to 65535(Hope so). So this is a very
lightweight small tool to make attackers fool as well as to increase the amount
of attack time with which you might trace the actual attacker.
References
http://www.centos.org/docs/4/html/rhel-rg-en-4/s1-iptables-options.html













No comments:
Post a Comment