In last part of this article if you can recall the network diagram, we have compromised gateway 192.168.101.6. In this article I am going to compromise ssh and terminal system which has IPs respectively 172.16.0.6 and 192.167.0.2.
In order to start our investigation, we will connect our lab machine through VPN credentials mentioned earlier. Now check for the reachability as shown below.
As usual we will start with port scanning. It was observed that two ports are up and running. One is mail server which is CommuniGate Pro and other is OpenSSH service.
Apart from TCP I also ran UDP scan for top 100 ports. It can be seen that Cisco VPN is available through its isakmp service which usually runs on 500 udp port.
I know many of you guys now started thinking about IKE aggressive mode enable. Its pretty famous Nessus result that we all get during our client's network security assessment. But there will be very few who exploits that in proper manner in order to get the internal network access or any other subnet whose direct access is not given to us.
In my previous post we have brute forced RalphWestfall's credentials to get into his SAS Bank account. I am assuming that, same credentials he might be using for the mail server access even. So trying to login using those same credentials.
Username : RalphWestfall
Password : freeman
I got the access of Ralph's email account. As usual try to find some juicy information. Here I found one email conversation between Ralph and his colleague. They are discussing about new VPN credentials. It pretty much clears that we have also found Cisco VPN device up and running on this gateway. So these credentials should be helpful for us to get the access.
However, in order to access the VPN, we required following details. Few of the details we have already obtained.
IPSec gateway address: 192.168.101.7
IPSec ID for 192.168.101.7:# (Some string/value which need to be find)
IPSec secret for #@192.168.101.7: # (Some string/value which need to be find)
Username: westfall
Username: westfall
Password: AiWa8ahk
Clearly green part of the data we have and red do not. However, I have no clue how to find IPSec ID and Secret key though. I ran nessus and it gave me a vulnerability named "Internet Key Exchange (IKE) Aggressive Mode with Pre-Shared Key".With the help of www.trustwave.com website, I started my assessment. This website has very good amount of 3 article series in which they are digging deep into this vulenrability. References are mentioned below.
In order to start our assessment, we require couple of tools.
- ikescan
- ike-force
- psk-crack
So I installed those pyip dependencies mentioned below.
Now it runs smoothly.
As IKE aggressive mode is enabled, tool did his work. From the output, our area of interest is highlighted. It is as below:
Encryption Algorithm - 3DES
Hashing Technique - SHA1
Authentication Mode - PSK
Group 2- modp1024
If you are curious how I got the MODP 1024 then you can visit here.In the documentation part you will get below table. You can read this about in the detail there.
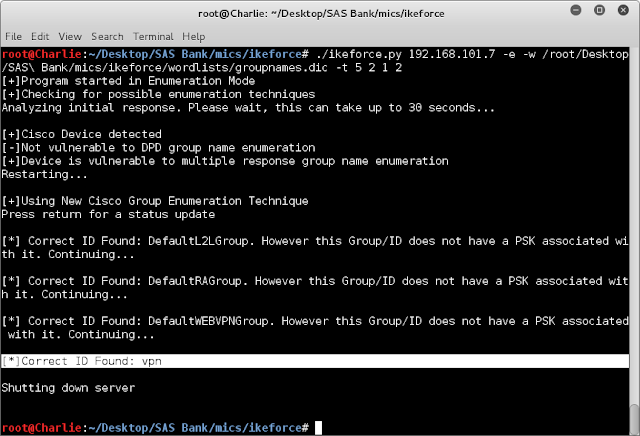
Now I will use ikeforce tool. IKEForce is a command line IPSEC VPN brute forcing tool for Linux that allows group name/ID enumeration and XAUTH brute forcing capabilities.
As you can see the tool has finally found the correct vpn id. Now we have below things in our plate.
IPSec gateway address: 192.168.101.7
IPSec ID for 192.168.101.7: vpn
IPSec secret for vpn@192.168.101.7:
Username: westfall
Username: westfall
Password: AiWa8ahk
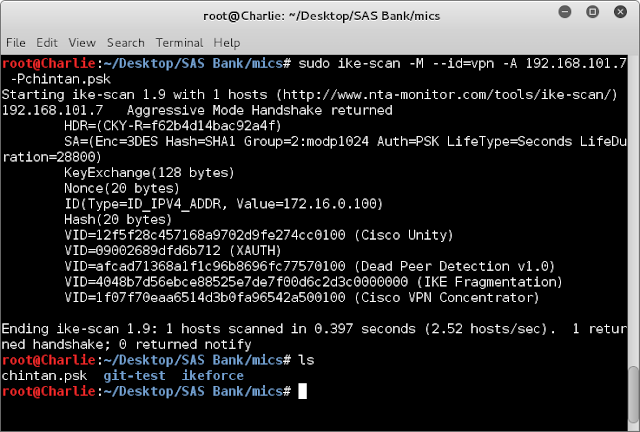
Now in order to find the secret key first we will try to capture the PSK handshake. And after cracking those handshake we may able to identify the secret key for our vpn.
As you can see chintan.psk would be created which contains handshake. Below is the PSK contents.
Now we need to crack it. For that we will be using psk-crack tool as mentioned below. I am using rockyou.txt password list in order to brute force. In order to download that refer reference link.
Now we have all information that we required to access the VPN. Lets sum up everything.
IPSec gateway address: 192.168.101.7
IPSec ID for 192.168.101.7: vpn
IPSec secret for vpn@192.168.101.7: cisco123
Username: westfall
Username: westfall
Password: AiWa8ahk
Try to login into the vpn using vpnc in-built command line tool as mentioned below.
It can be clearly observed that using all those information, I am able to login into the VPN and VPN has started running in the background. In order to confirm that VPN has actually started you can check it through ifconfig command. One new interface would appear in the list.
In my case it is tun1
Adittionally you can confirm your connectivity by pinging 192.168.0.2 host as we want to gain the internal network access. In our case, the terminal IP is accessible.
Performing the port scan for terminal IP. As mentioned below, few ports are open.
I ran nessus scan against these open ports and IPs. It gave one high finding which is ms08-067. I immediately opened up the metasploit and here are my options that I set.
I am ready to exploit now. Exploit was successful and one meterpreter session was opened. Then i manually crawled each and every folder within the windows system in order to find the token value. However, I could not find anything. Additionally it was very tedious to navigate through the command line. So I decided to add one user in the system. Not only that using this method I am going to add that user in the AD (Domain Controller). So as mentioned in the below screenshot, I have added that user with username chintanoscp and password as chintan@123.
Now logging into the system using that chintanoscp user.
As you can see that it was possible to login using our newdly added user. For my curiosity I wanted to check, how many different users are added on this system. For that I went to computer management and checked for the users under Local Users and Groups. Interestingly I found the token for Ralph user. It was our flag.
Now I am searching for the word token in the entire Documents and Settings folder. However, I ended up with nothing. I wanted find another clue/token for the rest of the system.
Interestingly I found key.ppk file on the desktop of wesfall's user account.I copied that to the C drive.
Downloaded key.ppk file through meterpreter.
I tried to get into ssh using that key. However, it gives custom error that permission to the file needs to be degraded.
Hence, I set this file's permission to 444.
Now again I am trying to access the SSH service using that file.
It is clear that once we got the access, token should be near around only. It was couple of minutes of hunt and here I got the token.
Hunt Over! Pawnd two nodes.
References:
- https://www.trustwave.com/Resources/SpiderLabs-Blog/Cracking-IKE-Mission-Improbable-%28Part-1%29/
- https://www.trustwave.com/Resources/SpiderLabs-Blog/Cracking-IKE-Mission-Improbable-%28Part-2%29/
- https://www.trustwave.com/Resources/SpiderLabs-Blog/Cracking-IKE-Mission-Improbable-%28Part3%29/
- https://wiki.skullsecurity.org/Passwords
- https://github.com/SpiderLabs/ikeforce
- http://carnal0wnage.attackresearch.com/2011/12/aggressive-mode-vpn-ike-scan-psk-crack.html
- https://github.com/trustedsec/ptf/blob/master/modules/exploitation/ikeforce.py




























No comments:
Post a Comment