If you have not seen the part 1 of this series then kindly refer that first. You must have seen that how I compromised site(172.16.0.1). Now it is time to attach the cabinet system which has IP 172.16.0.2.
Here is the revised network diagram.
Let me show you the nmap result of scanning gw 192.168.101.6 again so that you can understand what we will target now.
Then I moved to another URL which has the same functionality and asking for two parameters. Without parameters it cant parsethe request.
I thought am I missing something, I went back to the data which I pulled from that array and found that I was targeting the wrong email id. No matter all the email ids are the part of that array, however there is only one email id with the keyword SAS-BANK. That was the clue which I missed.
I found my token(flag). Game over Cabinet!
Here is the revised network diagram.
Let me show you the nmap result of scanning gw 192.168.101.6 again so that you can understand what we will target now.
So, in our part 1 of this series,I attacked on port 80 and was able to compromise the site mentioned in the diagram. Now I am going to target port 443 hoping that it must be the cabinet 172.16.0.2. SSH is also mentioned in diagram, however there is not any ssh related port open in our scanning result. Hence it can be clear that targeting port 443 will compromise the cabinet system.
First I opened the ip in the browser and it landed me on the login panel. Site does not have any other pages except login. Tried couple of injection techniques. Did not work.
I also tried scanning and spider through burp. Did not work.
Let us run our dirb quickly as we ran in our part 1 using custom user agent string.Dirb gave me the clue that folder api is accessible.
Accessing api folder it gave another clue that I can only access api/auth or api/balance.
Opening api/auth it looks like json response coming to us where email and password looks like a parameter name and they are seeking for their values.
Let us quickly craft the custom GET request and check if parameter works fine or not. It seems that both parameter worked fine however we need to find email id. From this page we can not identify which email id it would be. I tried couple of email ids including the one which is registered in lab.pentest.ru. It did not work.
Then I moved to another URL which has the same functionality and asking for two parameters. Without parameters it cant parsethe request.
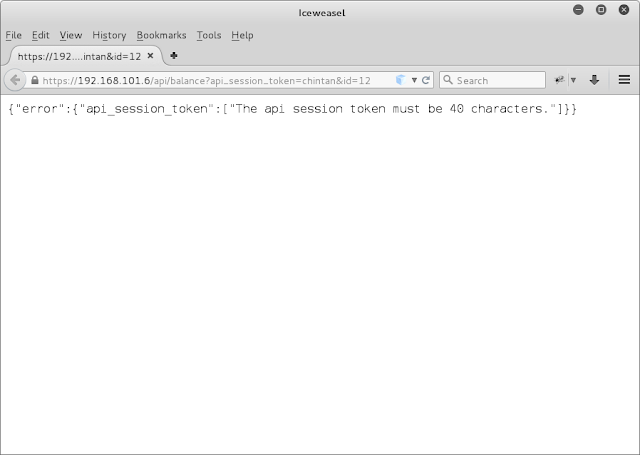
Crafted custom request manually and it gave me the error that token length must be 40 characters.
I crafted token length to 40 characters and it responded me with []. I analyzed the response in the burpsuite and found that it was a json response. It looks like [] some kind of array which may store some information.
What if we try SQL injection in order to fetch the whole data of this array. I tried with SQLmap but no luck!. Then i started digging manually.
I tried through repeater and was not able to find something.
I realized later on that there is some issue with the total length of the api_session_token parameter value. Since it only accepts 40 characters, after 40 characters whatever payload I give, it will reject. Hence I need to craft my payload in such a way that it complies the rule of the 40 character length.
Request:
Response:
Complying the length of the 40 character including my payload triggered the injection and application responded me with all data that was stored in the array. Result is displayed in the browser.
I picked random email id and crafted new request to the api/auth URL. It seems that all email ids are correct.
I decided to bruteforce password using john's most common password list. By default it will be in the /usr/share/john directory named as password.lst.
So I configured burp to test all these passwords against that particular email id. Here I am seeting Grep-Extract option in oder to find my result quickly. To know more about this tool you may Google. Click on Add button.
Since I know that majority of password will go fail so I am selecting just error word through the fetch response panel. It will list all the request in which error word is there in the response. So the clue is any request without that word can be the right password.
Unfortunately I did not found any password after testing all 3546 passwords against that email id.
I thought am I missing something, I went back to the data which I pulled from that array and found that I was targeting the wrong email id. No matter all the email ids are the part of that array, however there is only one email id with the keyword SAS-BANK. That was the clue which I missed.
I repeated same brute force again using this email id now. I found that password for this email id was 'freeman' as in the response it assigns one token and does not give any error.
I logged into the application through RalphWestfall@sas-bank.lab & password as freeman. I successfully logged in. Crawling through the application there is no any dynamic content expect upload profile pic on the top left corner under the logo.
Now I am uploading the legitimate file.
Using firebug, I was able to find the location where profile pictures are getting uploaded.
However, uploads folder was not given access to any user.
If you can closely observe from the below screenshot, uploaded files can be accessed with their original name only. That is the clue. If we are able to upload the shell and if we can access by it we may trigger something.
Since, application was in PHP so I wrote a simple PHP backdoor and named as chintan.php
I uploaded the simple php backdoor. Initially it gave me error at client side that only Image files can be uploaded. However I tried executing below URL as I know file could be uploaded on the server even though it gives error at client side.
I found that my shell was actually uploaded on the server and i was able to execute system commands through it. For testing I gave, ifconfig command and application gave me the result of that.
Now I have to find some juicy information. Initially I gave ls command to check in which directory I am and what files are actually lying in that.
I was in a search of juicy application files so I thought to navigate in /var/www folder where all application related files are placed normally.
Inside www folder I found there was a file named as token.txt.
I quickly run cat command in order to see the content of that file.
I found my token(flag). Game over Cabinet!
Reference:
- http://srandlabs.blogspot.in/2012/11/sql-injection-with-json_28.html


































1 comment:
WTF bro ! U R a pro ! Genius Work !
Post a Comment